Information technology has permeated every area and every aspect of our lives. Society as a whole has made such large strides in digitisation in recent years that now practically every area of activity is assisted –or even governed– by an information system.
On public transport, fewer and fewer people have printed tickets; the popularisation of internet access has taken us from the almost romantic image of the information superhighway to a situation where being connected is all but compulsory: anyone who lacks a mobile phone cannot share in the benefits brought by digitisation. Law 11/2007 on remote public access to government services has reduced the need to deal with paperwork face-to-face to a minimum. The universal, ubiquitous access to the internet, which has enabled globalisation and purchasing from outlets in the other countries, has also given rise to new risks and threats. Connecting to the internet opens up the possibility of anybody, from any continent, being able to come through our virtual front door and interact with our physical machine.
And if that is happening to individuals, the need to ensure digital security is even more pressing for businesses and organisations, particularly in sectors classified as critical, such as transport. The definition of cybersecurity is simple: it is the application of the idea of physical security to the virtual realm, created by computers. Security breaches, like accidents, cannot always be prevented but a clear plan and strategy can enable us to create the required capacity and prepare ourselves.
Ineco is working on different fronts and in different sectors and support systems for rail and air transport networks to create methods, strategies and internal policies, including training. As part of that work, we are preparing measures and action plans to resolve incidents on railway networks, satellite navigation systems and critical infrastructure. It’s a matter of helping organisations to be more cybersecure, in the broadest sense of the word, both in the physical world and in the digital world, helping them to anticipate problems; to develop cybersecurity habits and cultures; to protect themselves; to critically review themselves and to make the changes required for them to remain focused on meeting their goals.
Ineco is working in sectors and support systems for transport networks to create methods, strategies and internal policies, including training
The new risks of digitisation
In 2008, it was reported that a 14-year-old Polish boy had generated chaos and caused four trams derail in the city of Lodz. The tools he used: a manipulated TV remote control, time and determination. In September 2016, experts at the USA’s Department of Homeland Security tested the vulnerability of a Boeing 757 on the ground. They were able to access the plane’s systems using radio waves. Fortunately, transport systems as a whole dedicate enormous efforts to technology and procedures at all phases of development and operation to protect themselves against such failures, whether intentional or not.
The Spanish Government’s Department of National Security recently published a percentage breakdown of the strategic sectors most affected by cyberattacks in 2019: transport was the sector most affected, with 37% of incidents, far above the 23.87% suffered by the finance-tax sector and the 23.77% in water infrastructure.
The consequences of a cyberattack on essential services such as energy, water, hospitals, and transport are not limited to monetary losses, harmed reputation and breaches of confidentiality, but also include harm to people and the environment. The industrial environment (Operational Technologies or OT) in which support systems for those essential serves are installed have specific features that set them apart both in terms of the typical security measures in traditional computer environments (Information Technologies or IT) and in terms of the possible consequences.
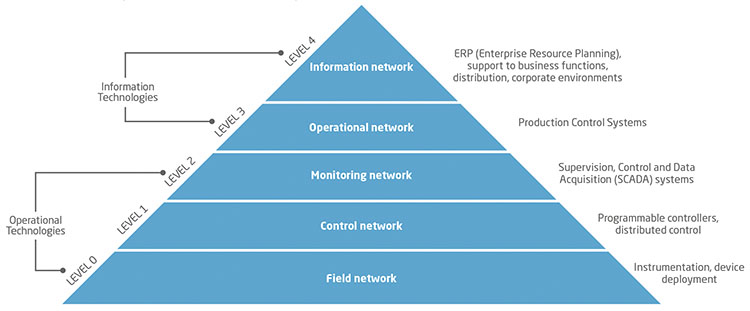
CYBERSECURITY IT (INFORMATION TECHNOLOGY) AND OT (OPERATIONAL TECHNOLOGY). The figure shows a classic structure for the elements of a an industrial/transport network, split into OT and IT. The boundary between the two is normally established at the higher levels of corporate systems. However, the current trend is towards rapid convergence at every level, thanks to the growing prevalence of IIoT (Industrial Internet of Things) items in field networks, the management of sensor alarms via mobile devices, etc.
Cybersecurity for critical infrastructure
In today’s society, certain services are essential to the continuity of basic functions: health, security, social and economic well-being, and the smooth operation of government institutions, which are referred to as ‘essential services’. The infrastructure that supports the operation of those services is known as ‘critical infrastructure’, meaning that there is no alternative. The operators of essential services and critical infrastructure, public as well as private, are required by the EU’s NIS directive to report all cyberincidents to their corresponding Computer Emergency Response Team (CERT), which in Spain is INCIBE-CERT for private sector operators and CNN-CERT for public sector operators.
For that reason, the State Secretariat for Security (SES) created the Office of Cybernetic Coordination (OCC) which is responsible for technical coordination and communication with those Spanish reference CERTs. The OCC’s move to place it directly under the SES last August (it was originally part of the National Centre for the Protection of Critical Infrastructure) demonstrates the ever-growing importance of cybersecurity within the National Security Strategy.
The National Centre for the Protection of Critical Infrastructure (CNPIC), working with Ineco and Leet Security, is promoting the protection of essential infrastructure and services
Given all of this, it is apparent that the capacity of critical infrastructure to maintain service continuity in the face of any malicious attack is absolutely essential. That capacity – resilience – has been a cornerstone of the protection of critical infrastructure from the beginning and has become one of the core principles of the National Security Strategy. To achieve resilience, it is essential to have a holistic, panoramic vision that creates a security culture.
Consequently, and in order to ensure that operators comply with the requirements to adequately protect critical infrastructure, the National Centre for the Protection of Critical Infrastructure (CNPIC), working with Ineco and Leet Security, is undertaking the creation of a certification scheme for the protection of essential infrastructure and services that will give visibility of security maturity in every part of an organisation. The scheme will have advantages both for government, providing an agile and effective tool for monitoring the security of critical infrastructure and its operators, and for operators themselves, who will be able to use certification to evidence compliance with their obligations under the Protection of Critical Infrastructure (PIC) Law and have a tool to understand and improve their level of security.
Cyberprotection measures in the rail industry
One of the objectives and successes of the rail industry since the beginning has been safety and security, using the tools available at different times. Today, the use of new technology assets that extend the capacity and performance of systems generates a new need: protection against cyberattack. The principal objective is to prevent harm to people, which translates in seeking to avoid situations involving risk of collision, derailment, etc.
The safety systems on a railway network include signalling that makes for efficient, safe use of the network. The system as a whole works on the basis that if a given problem arises, the safety level will go up. The highest level is ‘All trains stopped’, which is actually one of the goals of a cyberattack: loss of availability.
The implementation of cyberprotection measures in the rail industry has some unique features: technology with very long life cycles (up to 25 years), a feeling of being protected as a result of using their own network infrastructure, and highly specific technology and protocols. The deployment of devices across tracks, stations, control centres, trains, etc. makes for highly distributed infrastructure. Digitisation is increasing the risk of cyberattack through the deployment of IoT devices across the infrastructure, the extension of the attack surface area through interconnection with external systems, greater public information and online sales.
For example, some of the protective measures in ERTMS (European Rail Traffic Management System): the Level 2 of this European standard for automatic train protetion is based on continuous mobile communication between a train and its control centre (GSM-R, Global System for Mobile Communications-Railway). Communications are encrypted to ensure the integrity of transmissions, because this is how the train gives real-time information about its position and receives instructions as to up to how far it can run and at what speed, depending on the state of the line and other traffic.
Addressing the cyberprotection of this system requires a holistic analysis, taking into account the level of security of the technology used (GSM, encryption algorithms), the maturity of linked processes ((keys distribution) and the skill level of the people involved (possible attackers, motivations, knowledge required, benefits, opportunities to act). Some public results from a general review of the system showed that the greatest risk is posed by attacks launched from within the network, by highly skilled staff against elements of the national railway implementation, not covered by the standard, related to the management of encryption keys and the interface with control centres. It was also noted that the use of the GSM-R (2.5G) communication network creates vulnerabilities that have already been in next-generation networks.
The trend towards digitisation in the industry will lead to greater efficiency and service quality, but also increased cybersecurity risks. Railway network support systems are massively adopting technology change. Communications networks have gone from using proprietary protocols over dedicated links to interconnected networks with open protocols. Mechanical and electrical components have given way to electronic components and the early stages of the deployment of the Industrial Internet of Things. Maintenance processes are already being carried out automatically and remotely. All of this brings new risks.
Several challenges face the rail industry, which of great importance because it is a critical infrastructure. A factor in its favour is its well-established culture of the importance of personal safety, reflected in the implementation of the certification procedures mandated by AESF (State Agency for Rail Safety). But there is still a ways to go: establishing a rail CERT for coordination at the national and European levels, moving towards implementation of standards based on best practices and, more generally, raising awareness of the risks generated by cyberattacks.
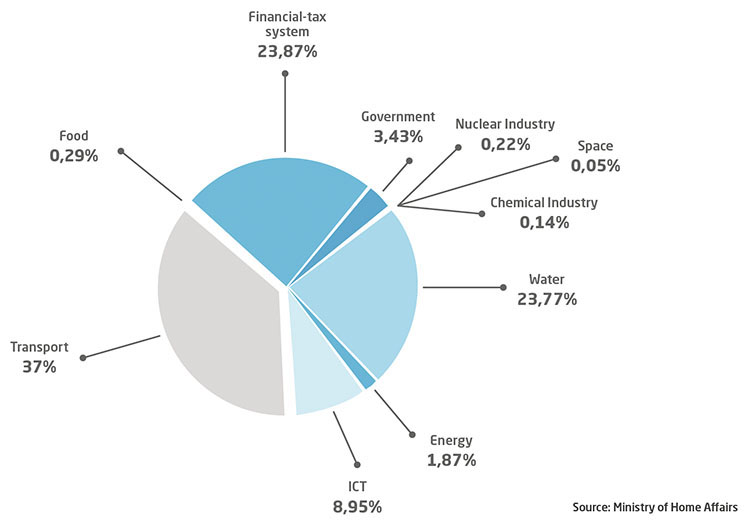
STRATEGIC SECTORS MOST AFFECTED BY CYBERATTACKS IN 2019.
The complexity of air and satellite navigation
Air navigation is becoming increasingly dependent on technology, principally ATM/CNS systems. The notion of CNS encompasses air communications, radio navigation aids systems and surveillance radar. ATM systems, on the other hand, are the systems that support air traffic control operations.
Because of these dependencies, cybersecurity in this area is exceptionally important and shares the features common to all OT (Operational Technologies) environments. The enormous complexity and high degree of interrelation of these systems are particularly noteworthy, with multiple information sources, stakeholders and components in communication with each other, which creates a very large attack surface. In operation, the most important things are operational security, integrity and availability. Confidentiality is less critical. Air navigation is also characterised by being based on legacy systems with a high replacement or update cost because they are loaded on a large number of aircraft. As a result, migration is slow and countermeasures have to be compatible with those legacy systems. Another characteristic specific to air navigation is that attacks can be made not just against data, but can also be electromagnetic (jamming, spoofing).
Ineco leads the activities of the Service Centre for Users of the Galileo programme, which provides services worldwide
Nevertheless, the importance of cybersecurity in air navigation is also due to the potential impact of a logical security breach, potentially triggering events that endanger the safety of an aircraft or affect continuity of service, and have other important effects (financial loss, reputation harm, etc.). The trend in air navigation is towards greater interconnection, the use of open standards, the growing use of general purpose market products and a move towards remote management. Those factors, together with the fact that cyberattacks are becoming increasingly sophisticated, lead to greater vulnerability. As EASA concluded in the Bucharest Declaration (2016), the concern is that the aviation system is insufficiently protected against cyber-threats, and there is an urgent need to develop a holistic response. The main organisations involved, such as ICAO, are already taking action.
The sector is also facing new challenges that will no doubt put cybersecurity at the heart of its further development, such as the concept of the smart airport, using the Internet of Things and SCADA (Supervisory Control and Data Acquisition) systems in airports and navigation; the implementation of SWIM (System Wide Information Management) with consequent greater interconnectedness; the proliferation of drones, and remote control towers.
Galileo, the European Global Navigation Satellite System (GNSS) is classified as an essential service because it provides PVT information (Position, Velocity and Time) for use in areas that are critical to public safety such as transport (aviation, maritime transport, self-driving vehicles, etc.) and in essential services such as business applications (agriculture, topography, etc.), unregulated applications (LBS or Location Based Services, IoT, etc.), finance, energy, telecommunications, and others. Consequently, given the critical nature of GNSS and its importance, it is essential to protect the system and implement security measures at various levels, such as accreditation of infrastructure and equipment for the handling of classified information and the implementation of cybersecurity measures in both ground-based systems and information systems on the satellites to protect information and communication.

EUROPEAN GALILEO SYSTEM: CYBER-PROTECTED SATELLITE NAVIGATION. Galileo is classified as an essential service because it used in many areas that are critical to public safety such as transport, business applications (agriculture, topography, etc.), location services, finance, energy, telecommunications, and others. As such, its protection, in which Ineco is playing an active role, is absolutely essential. / PHOTO_GSA
In the case of satellite navigation, the protection of navigation signals sent by users is fundamental. Currently, the two biggest threats are jamming and spoofing. Jamming consists in the emission of RF (radio frequency) signals that are stronger than and otherwise similar to the target signal with the aim of blocking that signal, making receivers unable to determine their position using the satellite signal. Spoofing, on the other hand, consists of generating signals that are analogous to those produced by GNSS systems and stronger than the GNSS system signals, with the aim of making the receiver tune to the false signal instead of the real one and thus receive altered location information, misleading it as to its true position.
Measures to counter these threats focus on different aspects of the user’s environment (antenna and receiver) and of the GNSS itself. For antennas, a controlled radiation pattern and adaptive beamforming, among others. For the receiver: multi-frequency (E1, E5 and E6), multi-constellation (GPS, Galileo, GLONASS, BEIDOU), hybridisation, monitoring of signal metrics, etc. For the system itself, the use of more robust modulations (MBOC, AltBOC), multi-frequency, PNT (Position, Navigation and Time) resilience, and authentication against spoofing. PNT resilience and authentication are two of the most important measures in the Galileo environment. PNT resilience is the convergence of GNSS with other technologies to improve reliability, performance and security. Authentication allows users to be sure that the signals they are using are being received from Galileo satellites rather than from any other source. Authentication is achieved by using public and private key encryption.